php文件被加密成如下所示的编码,直接找“黑刀威盾解密专家”
温馨提示:这篇文章已超过1036天没有更新,请注意相关的内容是否还可用!
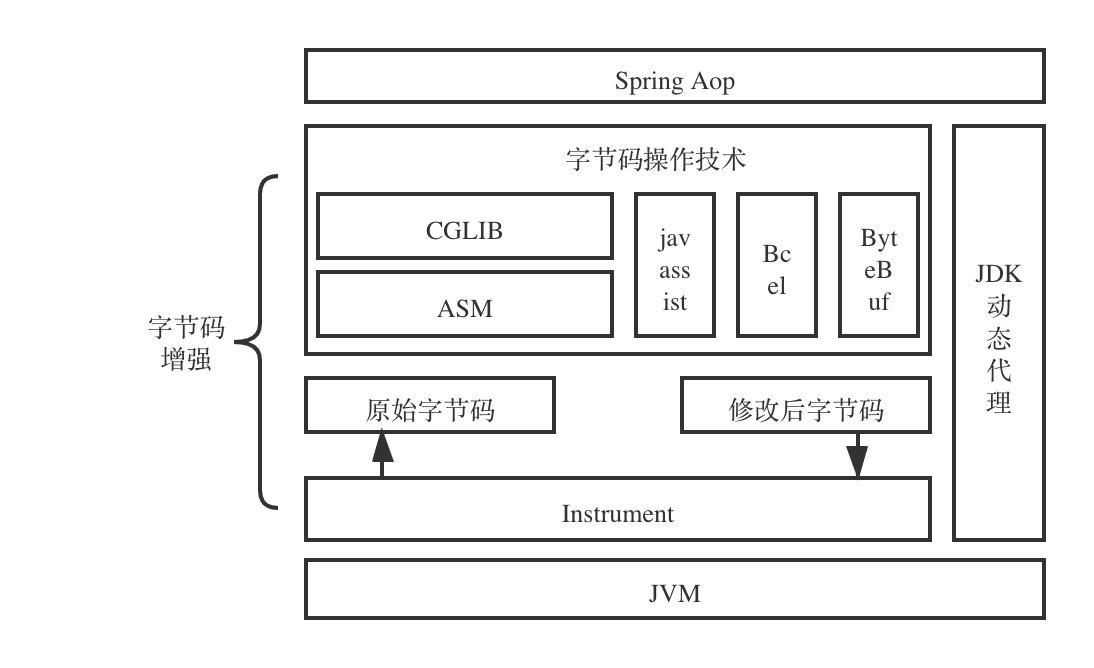
最近开始鼓捣,在论坛上下了某大牛提供的类库编码,文件是php文件,被加密成如下所示的编码,当前文件为原始文件就命名为:0.php吧。
36A4wWlv3WaVCNM42Ifn+GlRp8E6pGJ4CWaa0KDHP1yLVuOu5ju17cm5dTT411d0SguAPkIKB5611y6QB5y81xqO7EwOvjM5sNovEXbX2Nrv3YzFut5ebhsm8fATNaEm9nL+UIBlbtBpNfV0bHBG8nn5T6fcvjXPL1gOvjfZ081/8n5Fpf5Fpf5F2i+nEaLHCio1sq+a0K3kinCr8fbkiHE1UtEtTtz28n5F8Po2pGJmUtEtTKM/8nL2pGJFpf5F0Kz28Po28PJF8PJvrfL2pfL2pGJF8HM/8PJFpf5F8PJFTKz28PJF8PJFpGJ4TK30wnVYCXAiqbbHphzF0OlHui4uuW7tEqaP963Oz8+fgnQo3f/esbAg3IzRD8hqwqbW+nA9waf68QrKgX9Q8W+82NE1rnhK9nzhz/3UNl4T8fQu8Qozla+lbbCiqhagsqrICWbXC6A4gXV1wqBeEYhHEOzQ3Z3RDivFp8UP+Gl6+PMB0H5Z0N/408VXs67eE6lvrf5FpGo2pf5FpK/dCiCAwKM/8n5Fpf5Fpf5F081=G94aEZreEaLHCioeEZz4wXEvpK/dgWbACWbH0KrGw6BnCqBnTbzBEWljUYzaDY9eDWQ1uHoIgWhHE6bn2ibnCtnRUt/drhL8zbrqzbrwrnAlbhokbb+hlaLoznbubK332N3+wO44wW7ATPlmpKJvb6amCWLOEHoubKJQTIf4UfhFEW7ab6btN6anTPlP+HRP+tJvNnAl8lF1UW74g6lMz6bIg654Uf+vEXLVCN5P+HRFTIUF+IUmp8JPUh+ACXhHgN5QpPEmpPsZuHz1p8f7wGf7pqF7p8f7p8f7wGh1p8f7wGf7p8f7wGf7p8f7p8h1pqF7p8h1pqF7p8f7wGh1pqF7p8h1wGf7pqF7p8f7pqF7wWF7p8h1p8f7wGf7wGh1p8f7p8f7pq71p8f7wGf7p8f7wGf7pq71p8f7……此处省略编码若干……
很少接触php加密php源码加密 怎么破解,所以刚起初蒙了,不清楚是如何加密的,就只好自动解密了。后来才发觉原来是用威盾解密的,网上也终于有了相应的解读工具,所以即使见到如前面所示的代码的话,直接找“黑刀威盾解密专家”这款硬件就可以了。
然而走了冤枉路,当好歹最后解密成功了,也知道了整个加密的过程,所以还是把整个自动解读的过程发出来和你们共享下吧,下面是解读过程。
1x0
发现0.php中存在eval,那么直接把eval替换成echo,修改后的文件为:1.php
36A4wWlv3WaVCNM42Ifn+GlRp8E6pGJ4CWaa0KDHP1yLVuOu5ju17cm5dTT411d0SguAPkIKB5611y6QB5y81xqO7EwOvjM5sNovEXbX2Nrv3YzFut5ebhsm8fATNaEm9nL+UIBlbtBpNfV0bHBG8nn5T6fcvjXPL1gOvjfZ081/8n5Fpf5Fpf5F2i+nEaLHCio1sq+a0K3kinCr8fbkiHE1UtEtTtz28n5F8Po2pGJmUtEtTKM/8nL2pGJFpf5F0Kz28Po28PJF8PJvrfL2pfL2pGJF8HM/8PJFpf5F8PJFTKz28PJF8PJFpGJ4TK30wnVYCXAiqbbHphzF0OlHui4uuW7tEqaP963Oz8+fgnQo3f/esbAg3IzRD8hqwqbW+nA9waf68QrKgX9Q8W+82NE1rnhK9nzhz/3UNl4T8fQu8Qozla+lbbCiqhagsqrICWbXC6A4gXV1wqBeEYhHEOzQ3Z3RDivFp8UP+Gl6+PMB0H5Z0N/408VXs67eE6lvrf5FpGo2pf5FpK/dCiCAwKM/8n5Fpf5Fpf5F081=G94aEZreEaLHCioeEZz4wXEvpK/dgWbACWbH0KrGw6BnCqBnTbzBEWljUYzaDY9eDWQ1uHoIgWhHE6bn2ibnCtnRUt/drhL8zbrqzbrwrnAlbhokbb+hlaLoznbubK332N3+wO44wW7ATPlmpKJvb6amCWLOEHoubKJQTIf4UfhFEW7ab6btN6anTPlP+HRP+tJvNnAl8lF1UW74g6lMz6bIg654Uf+vEXLVCN5P+HRFTIUF+IUmp8JPUh+ACXhHgN5QpPEmpPsZuHz1p8f7wGf7pqF7p8f7p8f7wGh1p8f7wGf7p8f7wGf7p8f7p8h1pqF7p8h1pqF7p8f7wGh1pqF7p8h1wGf7pqF7p8f7pqF7wWF7p8h1p8f7wGf7wGh1p8f7p8f7pq71p8f7wGf7p8f7wGf7pq71p8f7……此处省略编码若干……
运行后输出结果如下:1.txt
$OO0OO0000=$OOO000000{17}.$OOO000000{12}.$OOO000000{18}.$OOO000000{5}.$OOO000000{19};if(!0)$O000O0O00=$OO0OO0000($OOO0O0O00,'rb');$OO0OO000O=$OOO000000{17}.$OOO000000{20}.$OOO000000{5}.$OOO000000{9}.$OOO000000{16};$OO0OO00O0=$OOO000000{14}.$OOO000000{0}.$OOO000000{20}.$OOO000000{0}.$OOO000000{20};$OO0OO000O($O000O0O00,1241);$OO00O00O0=($OOO0000O0($OO0OO00O0($OO0OO000O($O000O0O00,552),'JoKGfhWYUr0Tp+u29zN8lbqisCgwE3DkMAtI/aXZv4xy1VmeF7HPnQ6ORBjd5LcS=','ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/')));eval($OO00O00O0);
用1.txt的结果替换1.php中那些echo,得到:1a.php
36A4wWlv3WaVCNM42Ifn+GlRp8E6pGJ4CWaa0KDHP1yLVuOu5ju17cm5dTT411d0SguAPkIKB5611y6QB5y81xqO7EwOvjM5sNovEXbX2Nrv3YzFut5ebhsm8fATNaEm9nL+UIBlbtBpNfV0bHBG8nn5T6fcvjXPL1gOvjfZ081/8n5Fpf5Fpf5F2i+nEaLHCio1sq+a0K3kinCr8fbkiHE1UtEtTtz28n5F8Po2pGJmUtEtTKM/8nL2pGJFpf5F0Kz28Po28PJF8PJvrfL2pfL2pGJF8HM/8PJFpf5F8PJFTKz28PJF8PJFpGJ4TK30wnVYCXAiqbbHphzF0OlHui4uuW7tEqaP963Oz8+fgnQo3f/esbAg3IzRD8hqwqbW+nA9waf68QrKgX9Q8W+82NE1rnhK9nzhz/3UNl4T8fQu8Qozla+lbbCiqhagsqrICWbXC6A4gXV1wqBeEYhHEOzQ3Z3RDivFp8UP+Gl6+PMB0H5Z0N/408VXs67eE6lvrf5FpGo2pf5FpK/dCiCAwKM/8n5Fpf5Fpf5F081=G94aEZreEaLHCioeEZz4wXEvpK/dgWbACWbH0KrGw6BnCqBnTbzBEWljUYzaDY9eDWQ1uHoIgWhHE6bn2ibnCtnRUt/drhL8zbrqzbrwrnAlbhokbb+hlaLoznbubK332N3+wO44wW7ATPlmpKJvb6amCWLOEHoubKJQTIf4UfhFEW7ab6btN6anTPlP+HRP+tJvNnAl8lF1UW74g6lMz6bIg654Uf+vEXLVCN5P+HRFTIUF+IUmp8JPUh+ACXhHgN5QpPEmpPsZuHz1p8f7wGf7pqF7p8f7p8f7wGh1p8f7wGf7p8f7wGf7p8f7p8h1pqF7p8h1pqF7p8f7wGh1pqF7p8h1wGf7pqF7p8f7pqF7wWF7p8h1p8f7wGf7wGh1p8f7p8f7pq71p8f7wGf7p8f7wGf7pq71p8f7……此处省略编码若干……
又发现了eval,那就再换成echo吧!遗憾的是,这样做不能受到正确的结果。原因是:
文件末有长期的类似64位编码的数据,这些数据必须包括了经过编码的程序代码。
开头的解码脚本从函数获得当前执行的文件名,然后定位到编码数据外部的某个位置(也许是开头或后面),解码并执行这些数据中蕴藏的程序。
从0.php变换到1a.php的过程中,开头的解码脚本的长度被颠覆,造成不能定位到恰当的位置。
在1a.php已经可以发现三个数字:、1241、552。但是,无法判定某些数字将使解码脚本定位到编码数据的那个位置。
目前只能预测这段解码脚本的步骤。先把代码整理一下,得到1b.php:
36A4wWlv3WaVCNM42Ifn+GlRp8E6pGJ4CWaa0KDHP1yLVuOu5ju17cm5dTT411d0SguAPkIKB5611y6QB5y81xqO7EwOvjM5sNovEXbX2Nrv3YzFut5ebhsm8fATNaEm9nL+UIBlbtBpNfV0bHBG8nn5T6fcvjXPL1gOvjfZ081/8n5Fpf5Fpf5F2i+nEaLHCio1sq+a0K3kinCr8fbkiHE1UtEtTtz28n5F8Po2pGJmUtEtTKM/8nL2pGJFpf5F0Kz28Po28PJF8PJvrfL2pfL2pGJF8HM/8PJFpf5F8PJFTKz28PJF8PJFpGJ4TK30wnVYCXAiqbbHphzF0OlHui4uuW7tEqaP963Oz8+fgnQo3f/esbAg3IzRD8hqwqbW+nA9waf68QrKgX9Q8W+82NE1rnhK9nzhz/3UNl4T8fQu8Qozla+lbbCiqhagsqrICWbXC6A4gXV1wqBeEYhHEOzQ3Z3RDivFp8UP+Gl6+PMB0H5Z0N/408VXs67eE6lvrf5FpGo2pf5FpK/dCiCAwKM/8n5Fpf5Fpf5F081=G94aEZreEaLHCioeEZz4wXEvpK/dgWbACWbH0KrGw6BnCqBnTbzBEWljUYzaDY9eDWQ1uHoIgWhHE6bn2ibnCtnRUt/drhL8zbrqzbrwrnAlbhokbb+hlaLoznbubK332N3+wO44wW7ATPlmpKJvb6amCWLOEHoubKJQTIf4UfhFEW7ab6btN6anTPlP+HRP+tJvNnAl8lF1UW74g6lMz6bIg654Uf+vEXLVCN5P+HRFTIUF+IUmp8JPUh+ACXhHgN5QpPEmpPsZuHz1p8f7wGf7pqF7p8f7p8f7wGh1p8f7wGf7p8f7wGf7p8f7p8h1pqF7p8h1pqF7p8f7wGh1pqF7p8h1wGf7pqF7p8f7pqF7wWF7p8h1p8f7wGf7wGh1p8f7p8f7pq71p8f7wGf7p8f7wGf7pq71p8f7……此处省略编码若干……
后来,便是一行行弄清解码脚本中每个函数的值,这样就可以看懂其运行流程了。例如$=('%74%68%36%73%62%65%68%71%6c%61%34%63%6f%5f%73%61%64%66%70%6e%72');,可以在其前面加一句die($);,就能发现这个函数的值是'r',接着能够受到其它相关变量的值,进行更换整理后得到:1c.php
36A4wWlv3WaVCNM42Ifn+GlRp8E6pGJ4CWaa0KDHP1yLVuOu5ju17cm5dTT411d0SguAPkIKB5611y6QB5y81xqO7EwOvjM5sNovEXbX2Nrv3YzFut5ebhsm8fATNaEm9nL+UIBlbtBpNfV0bHBG8nn5T6fcvjXPL1gOvjfZ081/8n5Fpf5Fpf5F2i+nEaLHCio1sq+a0K3kinCr8fbkiHE1UtEtTtz28n5F8Po2pGJmUtEtTKM/8nL2pGJFpf5F0Kz28Po28PJF8PJvrfL2pfL2pGJF8HM/8PJFpf5F8PJFTKz28PJF8PJFpGJ4TK30wnVYCXAiqbbHphzF0OlHui4uuW7tEqaP963Oz8+fgnQo3f/esbAg3IzRD8hqwqbW+nA9waf68QrKgX9Q8W+82NE1rnhK9nzhz/3UNl4T8fQu8Qozla+lbbCiqhagsqrICWbXC6A4gXV1wqBeEYhHEOzQ3Z3RDivFp8UP+Gl6+PMB0H5Z0N/408VXs67eE6lvrf5FpGo2pf5FpK/dCiCAwKM/8n5Fpf5Fpf5F081=G94aEZreEaLHCioeEZz4wXEvpK/dgWbACWbH0KrGw6BnCqBnTbzBEWljUYzaDY9eDWQ1uHoIgWhHE6bn2ibnCtnRUt/drhL8zbrqzbrwrnAlbhokbb+hlaLoznbubK332N3+wO44wW7ATPlmpKJvb6amCWLOEHoubKJQTIf4UfhFEW7ab6btN6anTPlP+HRP+tJvNnAl8lF1UW74g6lMz6bIg654Uf+vEXLVCN5P+HRFTIUF+IUmp8JPUh+ACXhHgN5QpPEmpPsZuHz1p8f7wGf7pqF7p8f7p8f7wGh1p8f7wGf7p8f7wGf7p8f7p8h1pqF7p8h1pqF7p8f7wGh1pqF7p8h1wGf7pqF7p8f7pqF7wWF7p8h1p8f7wGf7wGh1p8f7p8f7pq71p8f7wGf7p8f7wGf7pq71p8f7……此处省略编码若干……
其中涉及文件操作的,也就是这几句:
$OOO0O0O00=__FILE__;//获取当前文件名 $O000O0O00=fopen($OOO0O0O00,'rb');//打开文件 fread($O000O0O00,1241);//跳过1241字节 $OO00O00O0=(base64_decode(strtr(fread($O000O0O00,552),'JoKGfhWYUr0Tp+u29zN8lbqisCgwE3DkMAtI/aXZv4xy1VmeF7HPnQ6ORBjd5LcS=','ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/')));//读取552字节,根据代码表替换字符,base64解码 eval($OO00O00O0);//执行解码后的代码
在1a.php中把eval替换为echo之所以行不通,就是由于此处写着的跳过1182字节。跳过1182字节是对于原始文件而言的,修改之后文件大小改变,需要跳过的字节数就不必定是1182字节了。现在,只要从原始文件中跳过1182字节后复制908字节,替换掉fread($,908),然后把eval换成echo就可以了,得到2.php
运行得到2.txt
while(time()>1445817600)die('参数错误,请检查参数!网络同步电视播放器(TV.LHKJW.COM)出品!');$OO00O00O0=str_replace('__FILE__',"'".$OOO0O0O00."'",($OOO0000O0($OO0OO00O0($OO0OO000O($O000O0O00,$OO00O0000),'JoKGfhWYUr0Tp+u29zN8lbqisCgwE3DkMAtI/aXZv4xy1VmeF7HPnQ6ORBjd5LcS=','ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'))));fclose($O000O0O00);eval($OO00O00O0);
再度出现eval,还是没有解完。将2.txt内容替换掉2.php的echo部分,然后再整理代码、分析各函数,处理方式就很显著了,从原始文件的编码数据开头起,跳过552字节,复制字节,替换掉fread($,),eval换成echo。前面那次解码使用的代码也必须删除,但是$=;这句要留着,因为里用到了这个变量。得到3.php:
1445817600)die('参数错误,请检查参数!网络同步电视播放器(TV.LHKJW.COM)出品!');
$OO00O00O0=str_replace('__FILE__',"'".$OOO0O0O00."'",(base64_decode(strtr($A,'JoKGfhWYUr0Tp+u29zN8lbqisCgwE3DkMAtI/aXZv4xy1VmeF7HPnQ6ORBjd5LcS=','ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'))));
echo($OO00O00O0);
return;
?>
运行完3.php,应该就可以得到解码后的源码了,解这代码,确实很费时间php源码加密 怎么破解,其实PHP是一个自由、开源的世界,既然肯将程序分享出去,就没必要将代码变成这种,影响执行强度不说,更是不利于修改、拓展,何必呢?
希望你们都自觉起来吧,对于引用的代码请标记出处,这样,分享者就不用这样麻烦了。
本文来自网络,如有侵权请联系网站客服进行删除







还没有评论,来说两句吧...